Just over 20 years ago there were genuine fears that the increasing dependence on IT would prove to be an ‘Achilles Heel’ for the world economy and society. Software may, or may nor, include a “bug” that could be triggered the closer to 2000 we got. It could cause chaos, many warned. The Archives of IT has a unique database of over 150 interviews of people who contributed to the development of IT in the UK. We have used the contributions made to the Archive to analyse what happened to this millennium bug, year 2000 bug or Y2K bug as it was variously called.
At the stroke of midnight as the new millennium started the screens of air traffic controllers would go blank. This would leave military and civilian planes flying blind, often unable to land and avoid mid-air collisions. Paul Fullager of the software company FCMC recalls: “I went to a couple of lectures on it, one of which – I wish I could remember the name of the fellow, probably just as well I can’t – who stood up and said that all the planes would stop flying and if they grounded them all there wasn’t room to actually land them all.” (Fullager Appendix of interviews) This is how a government pamphlet sent to all households in the UK in 1998 described the bug and its effects: Others predicted that billions would be wiped from the computerised bank records of individual and corporate customers causing widespread chaos of bankruptcy. One predication was that a month’s interest calculation could lead to a $10,000 savings account to show that the account was overdrawn by $493,401.48 at the end of the month. (Ludwig 12) The problems would not all be seen as the clock struck midnight. On Thursday January 6th 2000 bank vaults controlled by security systems with em bedded controller processors may refuse to open as in 1900 that date was a Saturday. (Craig and Kusmirak, p20) Employees could also be locked out of building by automated security systems on that day. The year 2000 was a leap year despite the general rule of thumb that years divisible by 100 were not. Billing cycles will be off: just-in-time supply systems will be off. (Hyatt 7) Even before the date change to 2000 these were problems. Some credit cards refused to recognise dates in 2000 and beyond. A grocer sued the supplier of cash register system as early as 1997 because the system crashed when presented with cards ending “00”. He had paid about $100,000 for the system in 1995 and sometimes the system would crash for five hours. (Hyatt 145) Some stock control systems signalled goods for destruction because they had a sell-by date later than December 1999. A system mistakenly ordered the destruction of tons of corned beef because the system calculated that they were more than 100 years old (Hyatt8) (Craig and Kusmirak p5) Accounting systems starting a new financial year on April 1, 1999 may have a problem because they would have to process dates in 2000. (Bramley and Halberstam 34) Inside the guts of pcs was a software system to handle input output (BIOS). Some 75% of pcs shipped before 1997 could not roll over to 2000 and thus would crash (Hyatt 23). Among the prophets was the Forrester Research Group which predicted that 300 of the world’s largest corporations would have serious failings in mission-critical computer systems. A half of all corporations would be slightly battered by the events of those minutes. (Feldhahn 6) John Handby, then CIO of a recently merged US/French pharmaceutical group Merial, says: “I guess when I first heard about Y2K I was sceptical. Could not really believe that such a simple thing could be a problem. But the technical guys around me at the time thought it was and, yes, the media were hyping it up.” (Correspondence with the author)
All this and more would be caused by the millennium bug: a software glitch caused by programmers trying to save storage when it was expensive and therefore not adding “19” in front of the date and just using two digits for the year instead of four. It was best practice for programmers to slice off the first digits of a date in order to cut the costs of storage and also improve processing time. “1978” became “78”, the “19” being added only when printed out. Thousands of bytes could be saved. The highest cost storage was within the computer processor: a kilobyte there cost $176 in 1975. (https://jcmit.net/memoryprice.htm accessed 9/7/2020) Then there’s the cost of storing the bytes on disk, tape or even perforated cards of paper tape. As well as these costs there is the speed with which it could be processed. Four bytes takes twice as long as two bites to shift about, use in a calculation or direct between devices. In all, therefore, when storage was expensive it was good practice to lop the first two digits off a date to lower costs and speed calculations. “1988” became “88” in the code processed and the data stored in the machine. The “19” could always be added later. Anyway, who writing in the late 1950s or early 1960s thought that software would last than long? And packages for the individual user often did not ask for the full four digits for a date in order to speed typing by leaving out the century. Computers of all types and sized are often sorting, and often by dates. Two-digit year dates seem to get suddenly smaller, making sorting a headache. A seemingly minor problem about 2000 but crucial in many applications such as cryptology, gambling and statistical sampling was that random number generators may crash. A much-used process was to start the calculation with the last two digits of the year and use that as a divider. But dividing by 00 would crash the generator. Solutions What was to be done? One thing not to be done was to roll the date forward before 2000 and see what happens. Bramley and Halberstam warn that the software may have embedded licences dates, see the date in 2000 and assume the licence has expired, and delete the application. Other software such as databases may have deletion dates in them and delete vital data which is still current. Further the whole system may refuse to start and the user may not be able to recover it. (46) There were three solutions. The seemingly simple answer to this problem would be to go through the programs and find out where they used two instead of four digits for the year. This was called date expansion. But there was a hitch: the programmers could have been coded in a low-level code for which the original documentation had been lost. And they could have been coded in a later higher-level code such as Cobol, turned into object code to run on a computer and, again, the original code lost or poorly documented. (Craig and Kusmirak p57) There were initially not enough programmers with knowledge of Cobol to go around: colleges and universities had stopped teaching Cobol in the early 1980s. Even if the documentation was available and there were enough people a single programmer could only correct about 100,000 lines of code a year with users such as General Motors having 2 billion lines, according to Trench. If date expansion was not possible the second approach was Windowing. Leave the year as two digits and assume it is 2000 or beyond. This is the simplest solution and the fastest. But there is a problem: perhaps it was in the 20th century not the 21st. And did two pieces of software which had to pass dates between them have the same windowing assumptions. (ibid) The third approach was to replace the software and/or hardware with new software and/or hardware. Many applications which had to be written bespoke in the 1970s and 1980s were now available as large packages which could be adapted to individual requirements. SAP, the German software company, had, for example, turned itself from a bespoke developer of financial accounting systems for the likes of ICI into a product vendor in 1978. In the five years running up to 1999 it grew its turnover by 66%, 47%, 38%, 59% and 43% year on year. (Campbell-Kelly 192-193) Accenture’s Ian Watmore says of the time: “So all the CIOs of the world said, ‘Y2K. Need a new suite and systems,’ and, and boards of directors said yes. So there was this massive splurge in, particularly enterprise systems, and of course SAP and Oracle were dominant things, but… And, and so, also, we started. get into CRM systems, with Siebel and so on.” (Watmore in Appendix of interviews) Handby then at the pharma group at Merial says: “In the run up to the millennium I was working as a CIO for Merial and therefore I was responsible for making sure that company did not suffer any problems. As it happens I had been brought in during 1998 to sort out an absolute mess of technology. Merial was formed from a merger in the pharmaceutical industry between a French and an American company and we operated worldwide. The company had no global network or common technologies – it was clearly broken and needed to be fixed. This was well understood and I was tasked with making it happen. So we had to refresh the technology completely and Y2K was great for us as it gave an imperative and clear timescale for finishing the work; which I used mercilessly on anyone who stood in the way!” (Correspondence with the author.) If not full replacement other vendors offered upgrades of conforming software and hardware. Roger Marshall who ran Y2K projects for local authorities says that some of the engineering firms were using Y2K to force users to upgrade: “and there was nothing you could do about it because we couldn’t test our software ourselves, it was all embedded, we had to trust them.” (Marshall Appendix of interviews) Even worse: there was not only one millennium bug but two. Most years divisible by 100 were not leap years. The year 2000 was an exception. Some some programmes may make the mistake of not adding Feb the 29 and jump from Feb 28th to March 1st His would invalid many calculations, Again, how to find out which did recognise it as a leap year and which software did not. Since the advent of the microcomputer and the pc in the late 1970s and early 1980s there had been an explosion of software packages for personal productivity applications. Many of these were written by programmers untrained in formal methods or rigorous programming techniques. A study by the UK consultancy Greenwich Mean Time in 1997 of 4000 pc-based software packages showed that 2,568 (64%) had problems dealing with the year 2000; of these 724 said they were year 2000 compatible. (Craig and Kusmirak p62) Microsoft and IBM were among the guilty vendors. Users of these pc-based packages did not get the original code so could not check it to see it was compliant. They got object code: the source code was the treasured crown jewels of the developers. The number of digital controllers with either hard-wired instructions or software running them had also exploded ever faster that the spread of micros and pcs.
The British Standards Institute developed a standard to test the compatibility of systems with the requirements to be safe when the millennium turned. It was published in 1997: This was prepared, the BSI said, in response to demand from UK industry, commerce and the public sector. It is the result of work by BT, Cap Gemini, CCTA, Coopers & Lybrand, Halberstam Elias, ICL, National Health Service, National Westminster Bank, taskforce 2000, Barclays Bank, British Airways, Cambridgeshire County Council, Computer Software Services Association, Department of Health, Ernst & Young, Federation of Small Businesses, IBM, ICI, National Power, Paymaster Agency, Prudential Assurance, Reuters and Tesco Stores. Such was the widespread concern about the Y2K bugs. The standard warned that checks should be made between claims to conformity and the ability to demonstrate conformity. In other words, don’t trust the word of the vendors of software. But standards were not enough if they could not be enforced. The US National Institute for Standards and Technology, settled on month and day, as in 7 April as 7/4. The UK British Standards Institute and the Canadian Standards Council reversed this to 4/7. Others used full stops, and some stared with the year. (Hyatt 54) Technical and contract inventory In order to find what had top be fixed you had to know what software and hardware you had: a full technical inventory was demanded. Few users of any size had one. Even more, Bramley and Halberstam advised users to conduct an audit on contracts as well as of technologies. Users should closely review all contracts with suppliers to see if they covered Y2K compliance. (76) BT by 1998 had already gone to the trouble of contacting 1,800 core suppliers warning them that unless they could show compliance with Y2K standards they would no longer be used by BT. The replies to these requests then became part of a case BT could take against any supplier whose equipment failed, The authors also advised companies to make a small payment to the supplier in order to make sure that the reply was a contract for which compensation had been paid. (Bramley and Halberstam 100 and 109) Halberstam was a lawyer with the lawyers Halberstam Elias and Co hence the strong focus in their book on legal issues. Bramley worked with Cambridgeshire County Council. As should happen in a book on Y2K co-published by the Institute of Directors, the authors focus on the legal responsibilities of directors, including non-executive directors.(155-162) How long would it take to fix the bugs and how much would it cost? Unlike almost every other software project there was a fixed deadline: no amount of money could stop the clock. Many organisations had millions of lines of code which may have to be checked. Probably the earliest any major organisation started to work on their Y2K problems was1989 when the US Social Security Administration started to audit its applications to scope out the extent of the problem. The Administration found that it had 30 million lines of code to review and repair. It took two years to finish the scoping. It then assigned 400 programmers full time on the job. It started fixing the code in 1991 and planned to finish at the end of 1998 in order the leave a year for testing. Yet after five years it had fixed six million lines, 20% of the total. (Hyatt 117-118). Even that was underestimating the issue: it had overlooked the 34 million lines of code in its many branch offices. It was not only Federal agencies which needed to fix their software. Individual states faced a bill of $75 billion to fix their software, Capers Jones, the American software engineer, calculated (Hyatt 120-122) In all in the public and private sectors there were billions of lines of code to be checked and hundreds of millions which would need to be changed. In 1997 the Giga Group Boston-based research company estimated that 50% of all companies were not going to make it. (Hyatt 43) In that 50% could be critical utilities such as gas, water, electricity and sewage.Rule 1. No value for current date will cause any interruption in operation. Rule 2. Date-based functionality must behave consistently for dates prior to, during and after year 2000. Rule 3. In all interfaces and data storage, the century in any date must be specified either explicitly or by unambiguous algorithms or inferencing rules. Rule 4. Year 2000 must be recognized as a leap year.
How much would it cost to fix the Y2K problem? The costs would have to be born by the users who wanted to have the bugs fixed as regular insurance did not cover the costs. The Association of British Insurers said: “Insurance is designed to cover the unforeseen and unpredictable. But the millennium is an entirely predictable and foreseeable event, and therefore policy holders are expected to prepare for and pre-empt any problems.” (Trench 47) Craig and Kusmirak were writing for a readership of small and medium companies with the imprimatur of the UK Department of Trade and Industry and the government’s Central computer and telecommunications agency. They advised these firms should put aside funds for: Internal staff time; External consultants which would become more expensive as time went on; The costs of audit to prove compli9ance; Legal fees and the costs of developing contingency plans; Upgrades or replacement of hardware and software; and even Stationary costs for invoices or statements for use with four-digit years and not two. (p40) A very rough rule of thumb, they say, might cost small and medium business £100 to £1,000 per pc to gain compliance. (ibid) Computing intelligence was thoroughly embedded in systems. For example there were 10,000 embedded systems in the North Sea oil and gas drilling and extraction operations. One company estimated it would cost $75,000 to test each chip on the sea bed. (Hyatt 28) As early as 1993 two billion microcontrollers were sold a year worldwide. (Hyatt 216) Taskforce 2000 reported in 1997 that of two seemingly identical pieces of equipment with embedded controllers, one was compliant and one was not. (Bramley and Halberstam 93-94) Chase Manhattan Bank put aside $250 million for Y2K repairs; AMR and Hughes Electronics budgeted $100 million; Federal Express wrote a budget of $500 million. (Hyatt 38) Chase had 200o million lines of code in 1,500 applications on 60,000 desktops, 400 midrange computers and scores of mainframes. Chase initially assigned 800 programmers and outside consultants. (Hyatt 97) In the bigger picture the Gartner Group estimated it would take $600 billion to fix the code. The bank JP Morgan in 1996 thought this was too high and estimated the cost to be $200 billion. It then revised its estimate closer to the Gartner projection: ”The Gartner Group’s $600 billion estimate may be as outrageously high as we originally thought.” (Hyatt 37) Notice that all of this expenditure, whatever the figure ended up at, was all being spent to stand still. No new applications or efficiency benefits would flow: it was aimed at making sure applications still ran. Hyatt quotes a users saying: ”This is a tough call politically, because after you spend the money [on Year 2000 fixes] all you’ve got is what you had before. It’s a hard sell.” (122)
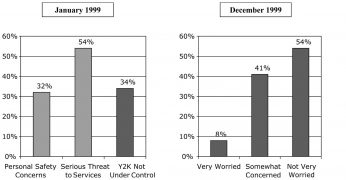
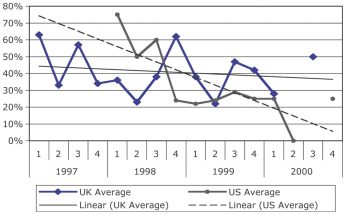
Articles started to appear in technology magazines the 1970s on the Y2K issue, then often called the Millennium Bug. The first time the UK government showed any public interest was in December 1995 when David Atkinson, Conservative MP for Bournemouth East. David Atkinson in a written question about what the government was doing about the non-recognition of 2000 in government and private sector computers. The answer was that there were several sources of information. Then in January 1996 Atkinson moved again: To ask the Secretary of State for National Heritage if she will make a statement on the problem of non-recognition by computers of the year 2000 with regard to her Department’s computers and those for which it is responsible. Mr. Sproat [answering for the Secretary of State] The Department of National Heritage is currently reviewing the necessity for any changes to computer systems to support the year 2000. (Hansard https://api.parliament.uk/historic-hansard/written-answers/1996/apr/03/computers#S6CV0275P0_19960403_CWA_15 accessed 1/7/2020) On the same day he asked through written questions another 14 government departments. The answer was much the same: some said they were coordinating with the government’s Central Computer and Telecommunications Agency in looking at the problem. On May 8th Atkinson asked another written question of the President of the Board of Trade Ian Taylor MP about a survey on the skills required to fix the systems. Ian Taylor replied: “The survey revealed a high level of awareness amongst IT directors of organisations. The technical skills required are not demanding, but the scale of an organisation’s problem can be reliably assessed only if an audit is carried out. The cost of fixing the problem depends on the size and age of an organisation’s software portfolio. My Department will provide information on our world wide web site, and through the business links, and will be persuading senior management to take the problem seriously. There is time to deal with it if tackled now. The longer it is left, the higher the likely cost of remedial work. I am urging all chief executives to discover now for themselves the extent of the problem in their companies.” By then Taylor had set up Task Force 2000 with government and private-sector funding. It had a skeleton staff of five and two consultants: one from the DTI and another from the US consultancy EDS. (https://www.independent.co.uk/news/business/labour-backs-taskforce-2000-1264754.html accessed 2/7/2020) The Conservative government of John Major did not have a strategy for Y2K, says Taylor. Major was frightened of technology: Taylor could therefore develop his own policy but it did not have prime ministerial support (Correspondence with the author). Taylor had developed his own policies and practices about IT as a result: he was the first minister to have an email, much to the concern of his civil servants; he had in 1995 made sure an report on innovation was available on line: the minister had wanted to charge for it but then it would “take a whole day to downlead at that time.” (Correspondence with the author). Taylor had started a campaign in 1997 called IT for All promoting the use of the Internet. In thinking about what would cramp the adoption of the internet Taylor and others identified the Y2K bug. Atkinson, who had asked Taylor what Y2K was all about and been encouraged by Taylor to keep digging, kept drilling into the subject for the rest of the year, presumably giving his Conservative colleagues in Government to opportunities to show how far they were on top of the issue. As early as January 13th 1997 Atkinson was on the case again, asking what was being discussed at European level about the Euro introduction and its impact on Y2K. The subject had been categorised by Hansard as Computers and Computer Systems: from late January onwards it was referred to as Century Date Change (Computers) or Computers (Century date change). (Hansard https://api.parliament.uk/historic-hansard/people/mr-david-atkinson/1997 accessed 1/7/2020). Atkinson did not miss an opportunity: Bill Gates met the Prime Minister Tony Blair in November 1997 and Atkinson asked him how the talks went over Y2K. Blair said Gates had briefly commented on the problem. Blair took up the issue and raised awareness of it through a number of speeches after his May 1997 election victory. He announced a reset of the tactics, even a strategy, in March 1998. He announced a further £97 million for what he called “bug busting”. He launched an organisation he called Action 2000 and a plan to recruit 20,000 “bug busters” to fix code. This put the nose of Task Force 2000 out of joint but that had been a Conservative Government initiative. Action 2000 was a more government-driven operation rather than the joint industry/government iniative of the conservative government Task Force 2000. Blair also appointed the Labour MP Paddy Tipping as minister for Y2K. Taylor saw him as a safe pair of hands. Blair knew he would be PM at the millennium and did want anything to go wrong. (Taylor correspondence with the author) The Archives has asked Tipping for an interview and he has nor replied. The Central Computer and Telecommunications Agency would look after government computing. The Department for Trade and Industry would liaise with industries. The Institute of Directors and the Confederation of British Industry would advise their members in the private sector as would the Federation of Small Businesses. The reporting structure in the UK government for the Y2K issue is as follows: One public outcome of the Blair initiative was the creation, publication and delivery to every home in the UK of a pamphlet What everybody should know about the millennium bug. It was a colourful 22-page booklet offering advise and available in 14 languages, in Braille, as an audio tape and in a large print version. From November 1999 Action 2000 had an ITV teletext page constantly updated. Very few people said that things would be OK. Of all those reviewed by Hyatt only three said things would be alright in the USA. He found three: Sally Katzen of the Office of Management and Budget, one article in USA Today, and one article in ComputerWorld. The media was criticised for creating a scare mentality about the bug. For example this exchange with the interview with Frank Jones of SEMA: Questioner: But wouldn’t you say though, that Y2K created an awful lot of fear, uncertainty and doubt and quite a bit of it was unnecessary? Frank Jones: Well, I could turn the tables back on you and say that was created by the press, rather than the… Questioner: We [the press] liked the story. Jones: You liked the story, rather than us. Taylor says the coverage given to fears of Y2K’s impact was important: “The press oversimplified it. But you do need a bit of oxygen. [The coverage] was very valuable.” (Correspondence with the author) Yet, the strength of headlines covering Y2K dropped off in the USA and the UK in the years before, according to Quigley. Percentage of articles with alarming headlines in The Times, The Financial Times, The New York Times and The Wall Street Journal Many vendors of services and software products commissioned surveys to identify awareness of the problems of Y2K. This is the announcement of a survey carried out for ICL in January 1999: “A new poll from ICL, the IT services company, finds that although awareness of the Year 2000 problem is now high amongst the British public (83%), many still believe that the country will face serious disruptions at midnight 31, December 1999. Almost a third (32%) of respondents feel that their personal safety is at risk, 54% see it as a serious threat to public services and more than one in three (34%) do not feel that UK organisations have the problem under control.” The countdown included reminders by the government that time was running out. This included public posters. Many writers linked the Y2K issues to their own agendas. Grant R Jeffrey in his book The Millennium Meltdown warned of world government which would be formed by the Antichrist in a book of some very useful practical proposals and yet alarming fears about the outcomes in the private and public sectors. Mark Ludwig in his book The Millenium (sic) Bug warned that the crisis would be an excuse to introduce a cashless society which would be a way of tracking every economic transaction of every citizen to make security overpower freedom.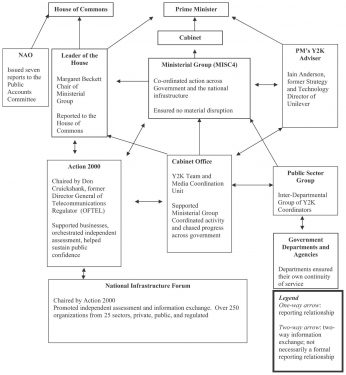
Source: Quigley

Source: Quigley
Source: Quigley

Six months before the new millennium the government, through Action 2000, pushed home the message to be prepared
Alistair MacDonald was a senior civil servant who had a team monitoring it in the Cabinet Office: “I actually had a team in the Cabinet Office ready all weekend so that, you know, if, if a hospital rang up… Every hospital had this telephone number to ring up if the electricity went down, and, what would we do in terms of crisis management? And, I personally remember very nervously, tentatively, turning on the television set at some point, probably about midnight, and seeing the new century celebrations taking place in New Zealand with fireworks et etcetera. And I saw, people had their lights on. [both laugh] Buses were running. [laughing] Well… Toilets were flushing. Oh my God! I actually… I thought, well, God, at least in New Zealand things haven’t collapsed. And, you know, by that evening, my team in the Cabinet Office had gone home.” (MacDonald Appendix of interviews) Dr Robert Nowill was at GCHQ monitoring the progress: “On the night itself I was on duty on the bridge, as it was called, one or two minor things cropped up, nothing of any substance, as turned out to be the case across the world.” (Nowill Appendix of interviews) The private sector was also looking on. Brian Collins, CIO of lawyers Clifford Chance says: “We watched Tokyo, because we didn’t have an office in Australia our furthest east office was Tokyo. So we waited for Tokyo to go through it all, and then Hong Kong actually, we waited for Hong Kong as well, and similarly went to sleep, if they’re alright, it’ll be alright. And it was. I mean there were one or two blips.” (Collins in Appendix of interviews) Handby was CIO at Merial the pharma group: “For Merial it was clearly worth it in that it gave an impetus for a much needed technology refresh. But I well remember the night of the millennium when (like everyone else) I was partying but in my case receiving calls from those countries ticking over first on whether there were any problems, starting with New Zealand. When we finally got to Italy and there were still no problems I rang the Chairman and told him it was a non-event. If there was not a problem in Italy then it was clearly a non-issue! Y2K was indeed froth and I am still surprised the techies were not more perceptive.” (Correspondence with the author.)
At 02.56 GMT on January 1 2000 the BBC website reported: “The millennium bug has failed to deliver the disaster scenarios predicted by the gloomiest commentators, but minor problems have cropped up.” “In Japan two nuclear power plants suffered problems but it was not confirmed as a YH2K problem. A flight weather information system also crashed.” “In Australia in two states bus ticket validation machines failed to operate.” “In the USA about 150 slot machines at race tracks in the US state of Delaware stopped working. But according to John Koskinen, who has been leading US efforts to tackle the Y2K bug, the machines have been fixed.” “In Canada, access keys to Defence Office safe rooms have been found non-Y2K compliant after tests.” “France’s national weather forecasting service, had the wrong date on a page of its website.” “The Spanish news agency Fee reported that a worker had been summoned to a tribunal on 3 February, 1900. A similar problem occurred in South Korea, where a district court issued summonses to 170 people for 1900.” “In the UK, hackers broke into the Railtrack website which provides online information on train times to travellers. They posted a message saying that because of Y2K problems no trains would be running in the country.” “Railtrack quickly corrected the site and stressed that trains would be operating according to timetables.” (http://news.bbc.co.uk/1/hi/sci/tech/586620.stm , viewed 19/6/2020) On January 20th 2000 Margret Beckett MP and Leader of the House of Commons told the House: “No Government Department has reported any significant problems. The alert status, contingency arrangements and staff cover of Departments and agencies over the date change meant they could deal quickly with the minor Y2K bug problems that were discovered. Across the national infrastructure, electricity, gas, water and telecoms as well as offshore oil and gas industries continued to operate as normal, and the markets and financial sector successfully resumed full trading on 4 January. The Government spent an estimated £380 million on tackling the millennium bug in our own systems, although without needing to make special further additions to Departments’ budgets. The investment made was both necessary and beneficial. Continued payment of benefits, pensions and child support could be ensured only by essential and major system changes. Many of MAFF’s internal systems, such as those for processing common agricultural policy payments on time, required corrective action or replacement. In the wider public sector, NHS trusts and Government agencies found problems that needed to be fixed. Problems in gas repayment meters and electricity prepayment meters were found and fixed. Elsewhere in the private sector—everywhere from finance to food and transport to telecoms—major potential problems were found and fixed, in time. There were, and no doubt will continue to be, further minor glitches. Here in the UK, a retailers’ card reader problem before the date change affected about 5 per cent. of terminals in shops, and hence the public. Although such problems needed to be rectified, there have been no further reports in either public or private sectors of problems which have caused a significant inconvenience to the public. The sorts of failures experienced typically have been incorrect date displays appearing on internal reports and read-outs. They have had no impact on customers. Those problems were corrected swiftly and had no impact on operations precisely because organisations were on the alert for problems and had put business continuity plans in place. The same pattern has been evident internationally—no material disruption, but concrete problems. For example, both France and the United States experienced problems with military satellites.” (Hansard https://hansard.parliament.uk/Commons/2000-01-20/debates/2280a17e-f3fe-4cd0-bd92-f4253d10c097/MillenniumBug accessed 1/7/2020)
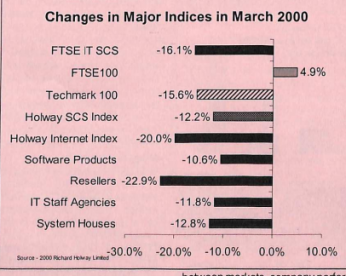
Why? Either the threat was not as large has had been projected by some or the efforts to repair and upgrade had been remarkable successful. The US President’s Council on Y2K established in February 1998 and which, among other things, provided a toll-free phone number for questions: 1-888 USA Y2K was led by John Koskinen who reported, with some relief, in March 2000: The Year 2000 problem was an extraordinary challenge for businesses and governments around the world that is not likely to be duplicated. The success that resulted from efforts to prepare systems for the date change is a tribute to the skill, dedication, and hard work of the countless professionals who made Y2K their cause. The story of Y2K is one of diverse organizations — industry associations, companies, and government agencies that often had opposing agendas and interests — coming together to recognize the power of information sharing and collaboration to achieve a commonly held goal. In its two years of operation, the President’s Council on Year 2000 Conversion worked to serve as a catalyst and facilitator for this activity, which helped the United States make a smooth transition to the new millennium. “We are, as a profession, hugely successful, and only very rarely is the public aware. Y2K, year 2000, all of a sudden, people suddenly were worried about whether the computers would go off at midnight on the 1 st of January 2000. By and large they didn’t, and, a lot can be said about the way the industry prepared and so on for that, some of it good, some of it not so good. But, my theme was that we were invisible engineers.” Roger Marshall in his London and home counties local authorities says: “As far as I’m concerned, as an IT person, it was a highly successful project. It was a project with a fixed deadline, we had enormously detailed project plans, because every bit of kit had to be evaluated and, if possible tested, and the plan all had to work first time. I’m very proud of that as a project.” Frank Jones from the outsourcers SEMA points to the work done: “The fact is, because the problem had been recognised early, it was like everything else, large amount of time and effort was devoted by all the companies and all the suppliers to sort it out. It was a problem, but it was solvable. If nobody had started looking at it until September, you know, ’99, we might have had a problem. But people were working on it for three or four years, so the problems were all solved.” Ian Taylor as a politician with his interest in IT says: “It’s easy to say there were no real problems in Y2K. Well, there were some. But overall, we succeeded in doing it. And that was a result of quite an intense amount of preparation for that. Yes. I mean, as I recall. I was ridiculed in many quarters for it, even back in ’96, well ’95, ’96 when I started to realise.” In charge of worldwide IT for the Clifford Chance lawyer partnership, Brian Collins points to the benefits beyond solving the Y2K problem which came from such close scrutiny of IT systems which had often grown with less discipline than need; “What people don’t talk about is all the corrective action they took and they never value that, because it was only tweaking a bit of software here and there, but actually if that had gone wrong and everything had been paralysed- and it’s like a lot of failure, you know, you don’t know what the cascading effect’s going to be down value chains and supply chains of loss, because remember e-commerce was just beginning to happen. So, you know, you would have lost trust and confidence in this company. Well, they didn’t see the bug coming so we’re not going to trade with them again, so you could imagine that could have happened. There were lots went on under the bonnet that people never talked about as to what they corrected. A lot of people discovered their system configurations they didn’t know, and one of the things we did was find out what your system configuration is, make sure all your operating systems are up to date, make sure all the version controls are right, make sure all the connections are right. Who’s accessing your machine is right, because those are the people who import bugs that you wouldn’t otherwise know about. So there’s a huge amount of systematic scrutiny, what you would call nowadays basic housekeeping, which is much more routinely done now. And a lot of people, particularly in the finance sector and in other engineering and in defence got their act together in advance and discovered all sorts of things that would go wrong, not necessarily millennium bug things that would go wrong, and as a result the whole quality of IT came up.” Only a higher quality of IT could provide a stable platform for what was coming: e-commerce. The older unaudited systems would not have been robust enough to form a platform for e-commerce which often linked parts of commercial systems never linked before. Watmore at Accenture makes the point: “Obviously the company worldwide made an absolute fortune out of it really, mainly because, not because of Y2K itself, which, we did very very little actual Y2K work, but because companies used it as the excuse to modernise their systems.” From his vantage of the London Business school Earl say the consequences as wider then fixing the bug: “And, as we know, it sort of went OK. What overtook it, I think, in the mixture of the business world and the technology world, and certainly in the business school world, was, before that 2000 date came, e-commerce came. And, so, certainly for our research purposes, and even more for our teaching purposes, e-business, e-commerce, sort of displaced Y2K as an issue. It was an issue, it was sorted, but it was that whole e-commerce thing. So, Y2K was an important issue, but it sort of, passed in the night a bit, and from my point of view, and I think actually for the IT world and business world, it was e-commerce that displaced it.” Covering the 15th anniversary of Y2K the BBC reported: “We achieved our aim,” says Gwynneth Flower, who was the managing director of Action 2000. “There were a few eccentrics. One woman virtually moved her whole family to a remote house in Scotland, with water only from a well at the bottom of the garden, because she thought it would be Armageddon. “With hindsight it is easy to say there was not a problem. Now we take all our vital services and their interdependencies for granted. “One of the banks we worked with confessed it was still processing all its transactions in pounds, shillings and pence with adjustments added on later. British Telecom has said some of its exchanges would have crashed. It only takes a tiny fault and the whole lot comes crashing down.” Not only did the users of IT benefit by having more fully documented and more fully tested systems but also the vendors. Unlike the coming .com bust this money did not evaporate but either stayed in the industry, went on salaries or went to shareholders. The Guardian online reported in December 1998: ‘Y2K has been a godsend,’ says Rusi Brij, a vice-president of Satyam Computer Services Ltd. The Indian firm has pioneered methods of debugging those computers which are programmed to use only two digits to signify the year. That practice, which began as a means of saving memory space, could lead to systems breaking down when January 1, 2000 dawns. “Hyderabad provides skilled programmers for the tedious task of trawling through millions of lines of computer code to correct the fault… ‘Anybody can enter into Y2K,’ S. Venkateswar Reddy says. ‘You don’t need to be technically qualified.’ He is a ‘body shopper’ – a hi-tech labour contractor who provides programmers to clients in Detroit at a price of 1,000-1,500 rupees (£14-21) for each recruit. Other body shoppers charge those seeking jobs up to 250,000 rupees, and their hunting grounds are the computer training schools.” (https://www.theguardian.com/world/1998/dec/30/millennium.uk accessed 20/6/2020) The dependence of the software and services sector on Y2K work is shown clearly by the down turn in IT markets in 2000 was the cash dried up. There were no major disasters to clear up. Susan Cuff was at Best Practice at the time: “There was a mini recession ’01 to ’03, 2000 of course was a damp squib, it didn’t provide the market with the fillip that we thought it would, it turned out that the country was much better prepared for 2000 than we thought they were. “ As the business dried up others vendors were hit. For example, Richard Christou had to radically restructure ICL in 2000 and was said to have saved the company. The collapse in business is evident in the impact on the share prices of software and service companies tracked by Systems House. In late 1999 shares were flying high: All of the indexes were up by strong margins. By April 2000 the picture was completely different: Although the FTSE 100 index was up everything to do with technology was down by as much as 22.9% for the share prices of retailers. And this was before the full force of the .com bust was really felt. Perhaps the largest impact all the effort to avoid the impact of Y2K had was on the management of IT and kits role in the private and public sectors. Braithwaite made a detailed study of the impact and identified 10 areas where the management of IT was, or should be, different as a result of the effort. In all he made 16 recommendations for action. Among the 10 areas are: Establish executive ownership of information and IT projects: Before the Y2K effort IT, if it was at all called that, was seen as just sophisticated clerical activity. After Y2K information becomes to be viewed as more of a source to be analysed and less a mere clerical recording of sales and inventories. Make improvements to IT management: Before the Y2K effort the IT industry had a poor track record of delivering successful implementations of technology. After Y2K it was realised that organisations should require and enforce accountability. IT vendor and supplier selection: Before Y2K selection was driven mostly by technical considerations; not enough attention was given to busines issues and management processes. After Y2K vendors would be held more to account for adhering to systems development criteria, would have to accept penalties for non-performance; and would have to support common user groups. (Braithwaite 115-161) Writing So soon after the Y2K efforts it is now evident that some of Braithwaite’s identification of changes in IT management were more aspirational than actually achieved.
Roger Johnson at Birkbeck College sees the work done by the IT profession in the run up to Y2K as the successful work of invisible engineers: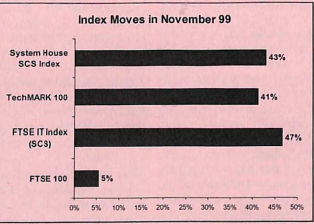
Over 80% of Y2K patches were achieved by windowing. There is a problem now emerging 20 years on, reported the New Scientist on January 7 2020: “Coders chose 1920 to 2020 as the standard window because of the significance of the midpoint, 1970. “Many programming languages and systems handle dates and times as seconds from 1970/01/01, also called Unix time,” says Tatsuhiko Miyagawa, an engineer at cloud platform provider Fastly. “Unix is a widely used operating system in a variety of industries, and this “epoch time” is seen as a standard.” “The theory was that these windowed systems would be outmoded by the time 2020 arrived, but many are still hanging on and in some cases the issue had been forgotten.” “Fixing bugs in old legacy systems is a nightmare: it’s spaghetti and nobody who wrote it is still around,” says Paul Lomax, who handled the Y2K bug for Vodafone. “Clearly they assumed their systems would be long out of use by 2020. Much as those in the 60s didn’t think their code would still be around in the year 2000.” Those systems that used the quick fix have now reached the end of that window, and have rolled back to 1920. Utility company bills have reportedly been produced with the erroneous date 1920, while tens of thousands of parking meters in New York City have declined credit card transactions because of the date glitch. “Thousands of cash registers manufactured by Polish firm Novitus have been unable to print receipts due to a glitch in the register’s clock. The company is attempting to fix the machines.” WWE 2K20, a professional wrestling video game, also stopped working at midnight on 1 January 2020. Within 24 hours, the game’s developers, 2K, issued a downloadable fix. Another piece of software, Splunk, which ironically looks for errors in computer systems, was found to be vulnerable to the Y2020 bug in November. The company rolled out a fix to users the same week – which include 92 of the Fortune 100, the top 100 companies in the US. “Some hardware and software glitches have been incorrectly attributed to the bug. One healthcare professional claimed Y2020 hit a system developed by McKesson, which produces software for hospitals. A spokesperson for McKesson [said] the firm was unaware of any outage tied to Y2020.” “Exactly how long these Y2020 fixes will last is unknown, as companies haven’t disclosed details about them. If the window has simply been pushed back again, we can expect to see the same error crop up.” “Another date storage problem also faces us in the year 2038. The issue again stems from Unix’s epoch time: the data is stored as a 32-bit integer, which will run out of capacity at 3.14 am on 19 January 2038.” (https://www.newscientist.com/article/2229238-a-lazy-fix-20-years-ago-means-the-y2k-bug-is-taking-down-computers-now/ accessed 20/6/2020) But then they were told even before Y2K. In early 1998 HPC Wire reported on windowing: “It’s a Band-Aid, the way building a house out of wood and fiberboard is,” said Jim Duggan, a researcher with the Gartner Group consulting company of Stamford, Conn. “You hope you’ll be somewhere else before it falls down. “It gets them off the hook,” agreed Michael P. Harden, president of Century Technology Services Inc. consultants of Fairfax, Va. “I don’t think some people expect to be in those same jobs. Fix it now, get everybody off your back — and in five or 10 years if there’s a problem, you won’t be around to have to deal with it.” (https://www.hpcwire.com/1999/03/19/common-y2k-quick-fix-last-decades/ accessed 20/6/2020)
Braithwaite, Timothy (2000) Y2K Lessons Learned, John Wiley, Chichester Bramley, Caroline, and Halberstam, Simon (1998) The Millennium Time Bomb, Institute of Directors and Kogan Page, London Campbell-Kelly, Martin (2003), From Airline Reservations to Sonic the Hedgehog: A History of the Software Industry, The MIT Press, Cambridge, Massachusetts Craig, Lynn and Kusmirak, Mike (1997) A Business Guide to the Year 2000, Kogan Page, London Feldhahn, Shaunti 1999, Y2K The Millennium Bug Resource Guide, Multinomah Publishers, Oregon, USA. Hyatt, Michael S (1998) The Millennium Bug, Broadway Books, New York Ludwig, Mark 1998, The Millenium (sic) Bug, American Eagle Publications, Arizona, USA. Jeffrey, Grant R (1998), The Millennium Meltdown, Frontier Research Publications, Ontario. Canada Quigley, Kevin F, (2005) Bug reactions: Considering US government and UK government Y2K operations in light of media coverage and public opinion polls, Health, Risk & Society, 7:3, 267-291, DOI: 10.1080/13698570500229770 Trench, William (1998) Millennium Bug, Durango Publications, Ontario, Canada
I thank all of those interviews for the Archives of IT who spoke about Y2K: their contributions on Y2K are in the appendix. Also to Ian Taylor and John Handby who contributed more material after their main interviews. Thank to Tom Abrams for his support as Editor in Chief of the Archives. Alan Burkett-Grey and Clive Couldwell provided essential background with their supply of cuttings on the subject. Steve Walker helped with vital background information. Finally thanks to Roger Graham OBE for taking his idea of the Archives and bringing it to life.
