Security can mean the safety of ourselves and our homes, data, computers and phones as well as the defence of our countries. AIT’s interviewees come from every industry concerned with all aspects of security. A selection of oral history interviews below give a deeper dive into this theme.
Defence
Armaments
Sir Julian Young KBE was the Royal Air Force’s (RAF) Chief Engineer, specialising in aircraft. He worked on the iconic Chinook helicopter and Phantom F-4 jets during the Gulf war. As his career (and the technology) progressed, software became more and more important both in the operation of, and safety of aircraft. In this clip, and talks about the importance of technicians and software programming skills:
“[aircraft] are nothing other than computer systems that just happen to fly; computer networks in themselves”
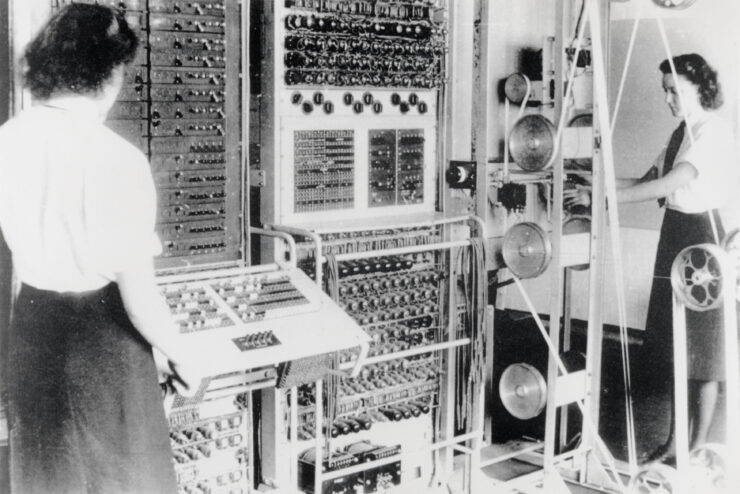
In this document, Joan M. Smith shares memories of her time working for AVRO including how to programme using an early Ferranti Mark 1 computer and its application to the creation of the Vulcan bomber aircraft. Read more here.

Systems
In the 1980s, David Thorpe ran various projects concerned with systems, both information and surveillance. Project Cedric was a surveillance system for shipping and aircraft – one of the very earliest monitoring systems of its kind, supporting operational officers from Her Majesty’s Customs and Excise. Project Unicorn, was a project to equip the Army with information systems that needed to be fully integrated with all its processes, battalions and regiments. In this clip, David talks about the culture at EDS, the company he worked at whilst they had a similar project with the Navy:
Cyber Security
We can think of cyber security as a more modern topic but cryptography – secure communications – has always been a concern. The Second World War saw the electronic computer come into existence with Colossus, used for code-breaking the enemy’s secure communications. Listen to our interview with Norman Sanders to find out more about those early computing pioneers.
Dr. Bob Nowill started work in cyber-security in the early days of GCHQ, who were looking at digital communications and satellites and their capabilities for defence. His career spans a rapid period of change in the field, from the Millenium Bug to the 9/11 terrorist attack and the development of cyber-warfare. Bob has been involved with significant security projects and legislation in the UK. Explore more by watching his interview.

We are as well placed as we can be to both respond to and keep up with those threats and opportunities. Having the right calibre of workforce engaged…in dealing with the threat and the opportunity is massively important.
The Dark Web
In our interview with Chris Hurst and Iain Johnston we explore what is meant by the ‘dark web’ and the ‘light web’ and its role in cyber violence. Both discuss their work building defences against cyber warfare in their interview, and how modern day conflicts are influencing the creation of cyber weapons.

The dark web is an industry, it is an ecosystem that exists in a parallel world to the light web, or the world that we actually live in. It’s a parallel universe to do certain things, there’s marketplaces, there’s communications, there’s messaging and so forth, but it’s all obscured.
Space
Space is a key part of defence, and is now a field of operation in its own right, alongside land, sea, air and cyberspace. Dr Andrew Rogoyski talks about his career in astrophysics, and his work in cyber security for space and defence clients in his interview. He talks about AI and some of its failures when applied to problems when it was expected to perform as an expert base. See this clip from his interview, where he talks about the downsides of expert systems, in this case when applied to a sonar project:
Danielle George is an Electronic Engineer who has worked on space projects including unmanned satellite spacecraft and the Atacama Large Millimetre Array, a series of 66 dishes working at super-high frequencies for radio astronomy. In this clip, Danielle talks about the future of space exploration, and what that might look like, as scientists and engineers think of ways to explore space using AI instead of more physically fragile humans:
Could we get to a point where we evolve and there’s this morphing of humans and Artificial Intelligence, and it’s that that then does the space exploration and it is that that colonises other planets if that is what we want to do, or explores other planets around the universe, not just in our solar system.